It’s true what they say; don’t believe everything you see on the Internet. More and more often, brands are getting hijacked (called ‘brandjacking’) by online scammers. With the rise of social media accounts and the internet age, brand impersonation is easier than ever, and hackers constantly develop new and creative ways of stealing a brand’s equity. Some stunts are short-lived, while others are a source of lasting damage for the targeted brand owners.
While large corporations are at more significant risk of brand hijacking than small businesses, it happens to companies of all sizes. Luckily, there are measures you can take to boost your security against imposters attempting to gain access to your customer base, secure information, and the like.
Below, we’ll cover the various types of brandjacking to be aware of, with examples, as well as what you can do to reduce the risk hijackers pose to your brand reputation and marketing campaign.
What is Brandjacking?
Brandjacking is when a company or cybercriminals assumes the identity of an unaffiliated, legitimate brand. Brandjacking is any activity conducted under the guise of being an official communication of the hijacked brand in question. It is a deliberate attempt to fool the public to steal an (often larger and more successful) brand’s identity, authority, or messaging. It often leads to a damaged online reputation as well.
Types of Brandjacking
Brand abuse comes in many flavors. Sometimes, it appears as the imposter blatantly lying about their association with the hijacked brand. Other times, it is a more subtle attempt to shift public perception. Brandjacking can sometimes be used to scam or poach existing customers, piggyback off a more established brand’s success, or create fake news about that brand. Below are some examples of the various types of brandjacking of which to be aware.
Cybersquatting
Cybersquatting is the unauthorized use of internet domain names that are similar or identical to the hijacked brand’s. It is done to trick the targeted brand’s customers and divert traffic from the legitimate site. By tricking customers into believing that they are accessing a company’s official website, cybercriminals can scam people into making purchases, revealing personal information, or conducting similarly damaging transactions.
For example, a cybersquatter attempting to scam Apple customers might register a domain name similar to Apple.com. To prevent cyber squatters from falsely conducting transactions, Apple has reserved domain names similar to Apple.com, such as Aple.com, redirecting them to Apple.com.

Phishing
Phishing is a direct attack on consumers, often in the form of fraudulent emails, text messages, phone calls, and online pop-ups that encourage a user to provide sensitive information. This information may be a bank account or credit card number, Social Security number, or password. Phishing can result in fraudulent charges, stalking, and even identity theft.
If you’ve ever received a suspicious email from an unknown sender or taken a call from someone threatening to shut your power off unless you pay them over the phone, you’ve probably been a target of a phishing campaign.
Identity Impersonation
Identity impersonation is similar to cyber-squatting, except that the target is a personal brand rather than a corporate identity. This form of brandjacking is especially prevalent on social media, where brandjackers can create false accounts for celebrities or public figures.
For example, in 2009, a cyber-squatter posing as Tony La Russa opened a Twitter account under the St. Louis Cardinals manager’s name. They then made offensive tweets with La Russa’s online identity.
Measures that Can Be Taken to Combat Brandjacking
Brandjacking can happen to even the most prominent companies — take Target, for example, which suffered one of the largest data breaches to date in 2013. However, there are plenty of ways you can prevent the PR nightmare that is brandjacking from happening in the first place. In addition to amping up your general cybersecurity, consider registering your business’s trademark, buying brand-related websites, investing in domain security, filing a trademark infringement claim, and creating a crisis management plan.
Register Trademark
Registering your trademark is a crucial step — perhaps the most important — in protecting your intellectual property. It’s best practice to register your trademark as soon as you file your corporation or LLC paperwork. If you don’t have a registered trademark, you are using your brand name, company name, or domain URL in an unprotected manner. That means that at any time, a brandjacking — or a legitimate company, for that matter — can swipe your name right out from under your nose, taking your brand equity with it.
Registering a trademark isn’t free, but it is necessary. You’ll receive rights and protections you wouldn’t have otherwise. In the long run, having a registered trademark will save you a bucketload of negative publicity and legal fees should you need to take legal action to protect your brand’s reputation.
Buy Brand-Related Websites
Holding a trademark is just the first step to brandjacking prevention. In today’s day and age, most, if not all, businesses have websites where they represent their brand to consumers. Simply owning a trademark does not entitle you to a particular domain name. To prevent other companies from poaching your business, consider buying not only the main domain but several others also.

Many companies, small and large, stomp out brandjackers by buying up website domains similar to their own. Sometimes cyber-squatters will brandjack by slightly altering the legitimate brand’s domain name, as with our Apple example above. They may tack on a phrase like .store, .press, .arts, etc., to the end of a brand name. Or, they might register a domain with a slightly different spelling than a legitimate website hoping that a careless customer will misspell the intended search term (fun fact: typing googel.com in the address bar will redirect you to google.com homepage).
In buying domain names similar to your company’s, you ensure that cyber-squatters, or other brands, do not cause accidental confusion or deliberate mayhem for you and your customers. Also, you can use multiple domain names to your advantage by either creating marketing campaigns for your brand or redirecting traffic to your main landing page. It’s good to be on the lookout for existing domains that are similar to the one you want so that you can avoid stepping on a competitor’s toes or being accused of cyber-squatting yourself.
Invest in Domain Security
A domain security policy is a means of protecting your consumer-facing landing pages from interference. This is accomplished through measures such as:
- Registry lock
- Domain Name System (DNS) hosting
- DNS Security Extensions (DNSSEC)
- Domain-based Message Authentification, Reporting, and Conformance (DMARC)
A well-rounded security policy should include an in-depth defense strategy, incorporate DNS and digital certificates of authenticity, and be proactive about identifying and responding to security concerns.
Create a Crisis Management Plan
Let’s face it: a brand crisis is the last thing a company needs. If poorly managed, a brandjacking incident can have a long-term impact on your public image, consumer and business relations, and revenue. Unfortunately, even if you’ve followed all the above steps to a T, disaster might still strike. Should the worst transpire, having a plan in place to handle the ramifications — short-term and long-term — of brandjacking will help you get back on your feet quickly.
A comprehensive crisis management plan has five phases:
- Assess the situation
- Assign roles to employees
- Engage stakeholders
- Have a good crisis communication
- Evaluate next steps and preventative measures
Trademark Laws and Regulations
You undertake a multitude of rights and responsibilities as a trademark holder — enough to sustain entire careers as a copyright and trademark lawyer. For the purposes of this blog, we’ve narrowed it down to just the need-to-know basics of trademark law. We recommend consulting an attorney for detailed instructions in setting up your trademark.

A good rule of thumb to know is that trademarks give you a scope of protection, but by no means is this protection total. Once you’ve registered a trademark, that trademark belongs to you. No one else may use that name. However, you can only trademark phrases that correspond directly to the goods or services you sell. You cannot trademark general words. For instance, you could trademark the name of a lead distribution software company called “Lead Bistro,” but you cannot simply trademark the term “lead” or “bistro.” Likewise, you cannot trademark generic symbols, designs, phrases, or words that do not indicate your product or services.
Common law rights mandate that if you haven’t registered a trademark in a state or federal database, your rights to that trademark only extend to your geographic area of operation. You will not be able to enforce trademark law outside these bounds.
There are three levels of trademark registration: state, national, and international. Below is a summary of each class.
State Trademark Registration:
- Not protected outside of the state you are registered within
- It can be applied to multiple states
- Not available in all states
Federal Trademark Registration:
- Rights apply to all U.S. states and territories
- Allows you to use the R symbol
- Trademark protected across state lines as a business expands
International Trademark Registration:
- It can be filed in multiple countries as long as you meet legal requirements
- Does not guarantee trademark will be recognized in all countries
- Single application form which is reviewed individually in each country applied for
Trademarks last forever, provided you use them in commerce and can provide evidence of this. You will need to maintain a federal trademark registration every five years.
For more information about trademark laws and regulations, you can review the United States Patent and Trademark Office’s (USPTO) website.
Trademark Registration Process
The step-by-step instructions for the trademark registration process, according to USPTO, are:
- Application
- Examination
- Publication
- Registration
Before you even attempt to register a trademark, you should search online for similar business names to make sure you aren’t wasting your time attempting to trademark a brand name that already exists. Try not to pick anything too similar to existing brands; you don’t want your customers to get confused. You want a name that will help you stand out from the competition.
Weird Brandjacking Examples We All Know
We see brandjacking in our everyday lives, even if we don’t realize it. You may have even been fooled before by misleading iconography, misspelled words, a fake account, or counterfeit goods of luxury brands. This is constantly happening on social media platforms like Facebook and Instagram.

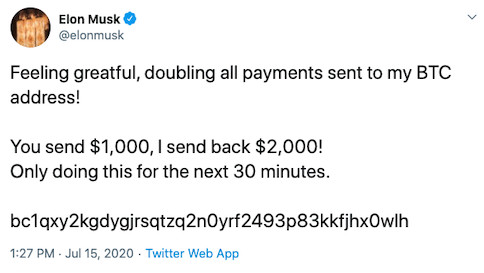
Twitter was the target of the most recent brandjacking scandal, in which several high-profile celebrities and famous brand Twitter accounts were compromised. Barack Obama, Joe Biden, Kanye West, Elon Musk, Apple, Cash App, and several others fell victim to hackers who stole their Twitter handles. The hackers assumed these celebrities’ online identities in an attempt to scam their followers into sending cryptocurrency to a mysterious address. The Twitter hackers made over $120,000 in bitcoin from unsuspecting users.
Here are a few more examples.
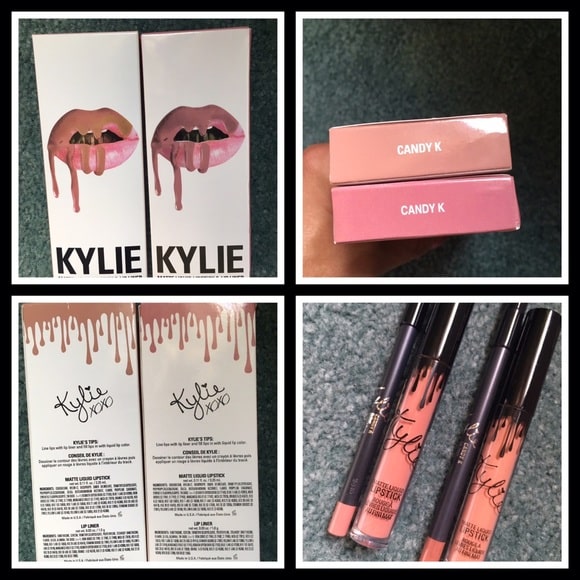
Kylie Cosmetics Fakes
Copycat Cereal Brands

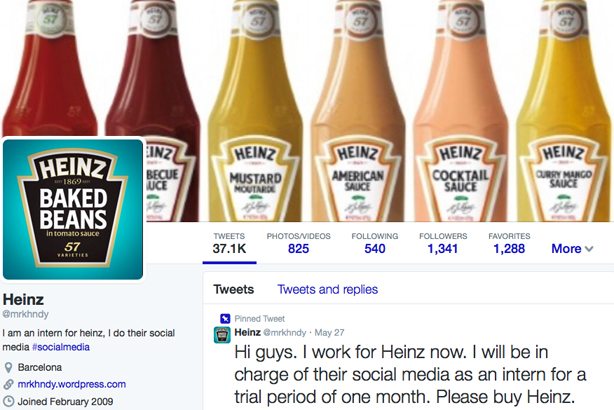
The Heinz Cyber-squatter
2020 Twitter Hack